Data Lifecycle Protection and Privacy
With privacy regulations brewing across the globe and consumers becoming more knowledgeable than ever about their privacy rights – can we now assume our personal data is now more secure than ever? Can organizations claim compliance with privacy regulations for all personal or regulatory protected data?
You cannot protect what you can’t find. A solid up-to-date inventory of all personal data is the first and most crucial step in complying with privacy regulations. The inventory must encompass data types, consent levels, usage, risks and how they map to regulations and standards. The end result paves the way to documenting the necessary policies and procedures that are also critical to ensure compliance.
Security by design simply means we implement the necessary controls to mitigate risk in everything that we do. Ranging from a server build to a cloud deployment – all steps must include security implementations to ensure continuous compliance and ongoing protection.
We must exercise due diligence in our efforts to protect what’s important and continuously comply with laws and regulations. Continuous visibility into personal data across its lifecycle is a critical first step to ensure compliance. Treating all types or personal data the same as it relates to risk mitigation, controls implementation and consent.
Get Your Free Score
SecurityScorecard offers an overview of your organization’s cyber security.
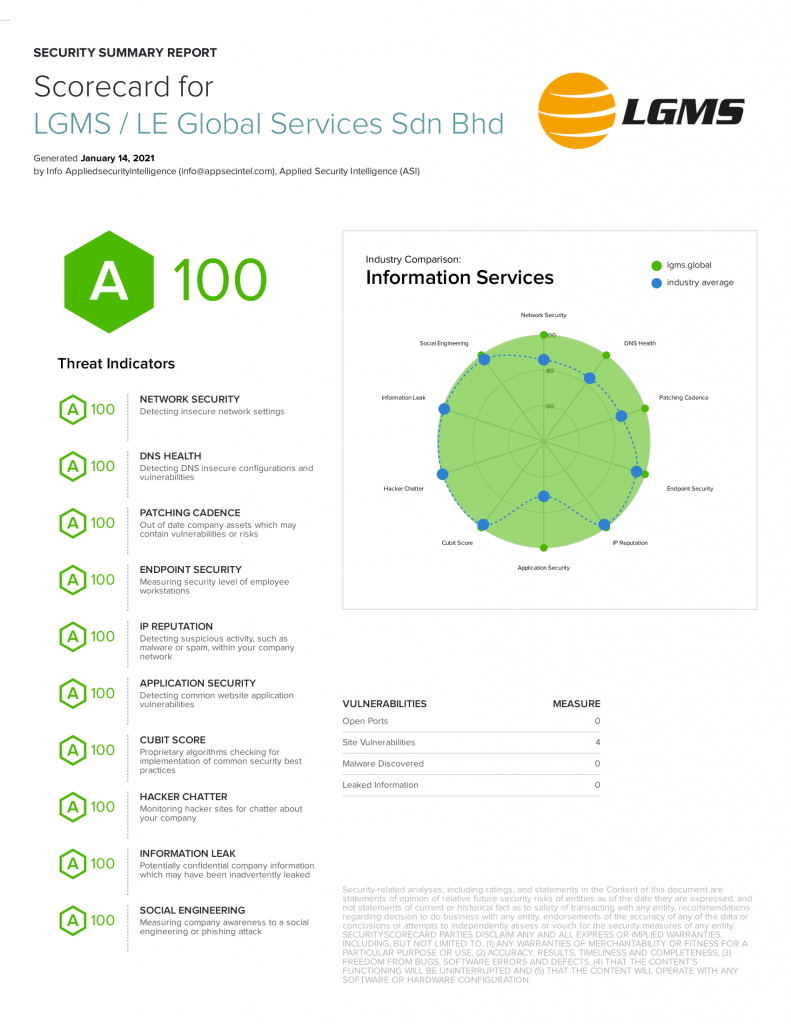

Founded in 2020, Applied Security Intelligence is a company under LGMS specialized in providing cyber security services with the help of threat intelligence.
Contact Us
Applied Security Intelligence Sdn Bhd (1391368-M) A-11-01, Empire Office Tower, Jalan SS16/1, 47500 Subang Jaya, Selangor, MalaysiaPhone: + (60) 3 8605 0155
Fax: +(60) 3 8605 0154
Email: [email protected]
Applied Security Intelligence | All Rights Reserved
